TL;DR – The UK Is Forcing Apple to Weaken Encryption – Here’s Why It Matters
The UK government is demanding access to encrypted iCloud data, forcing Apple to disable Advanced Data Protection (ADP) for users in the region. This move has massive implications for digital privacy, cybersecurity, and the future of encrypted services.
Key Takeaways:
- Apple’s Advanced Data Protection (ADP) is gone for UK users, meaning iCloud backups are no longer end-to-end encrypted.
- The UK Home Office is using the Investigatory Powers Act (IPA) 2016 to justify its demand, arguing it’s needed for law enforcement.
- Without encryption, government agencies, hackers, and cybercriminals have a much easier path to accessing personal data.
- Apple’s compliance sets a dangerous precedent—WhatsApp, Signal, and Google could be next.
- UK users now face greater risks of surveillance, data breaches, and identity theft.
- Privacy-focused companies may leave the UK, rather than compromise security.
- Users can still take steps to protect their data, like using local encryption and alternative cloud services.
This is a defining moment for digital privacy. Read on to see how this could affect you—and what you can do about it.
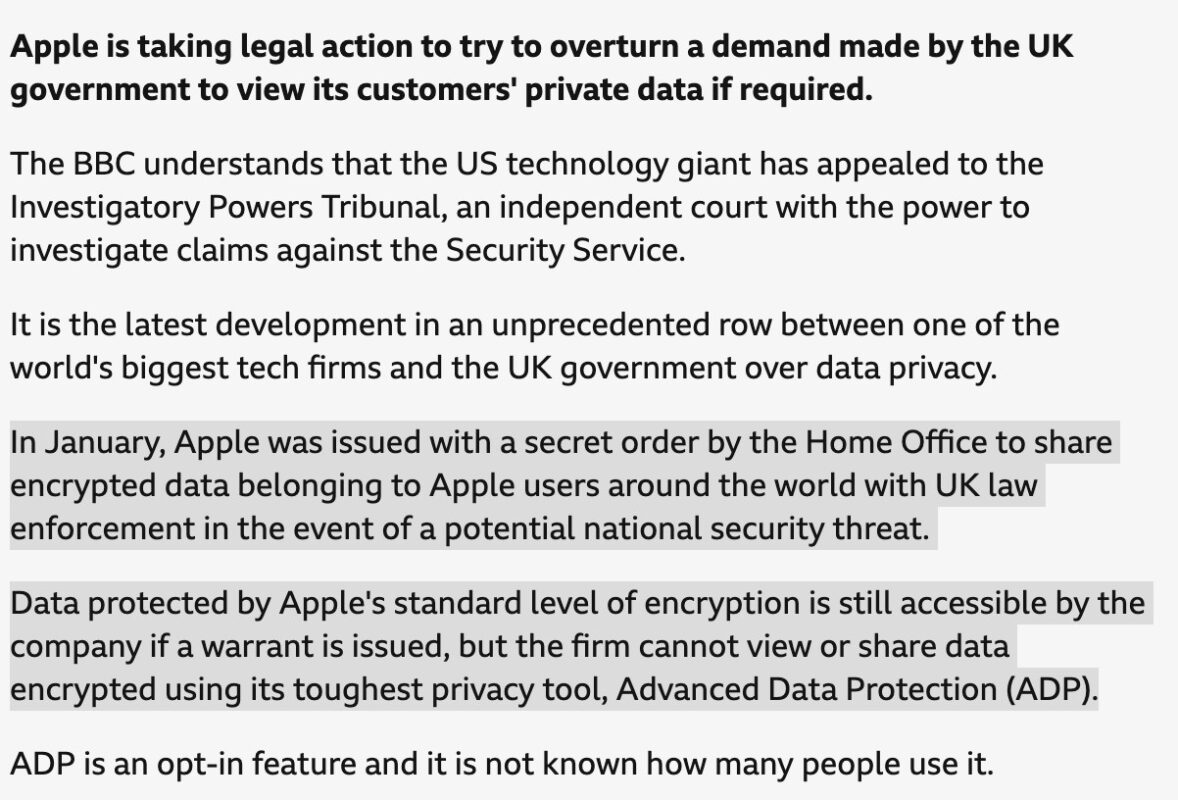
The UK government is demanding access to encrypted iCloud data, forcing Apple to disable its Advanced Data Protection (ADP) feature for users in the region.
This move ignites a global debate over privacy, security, and the ethical responsibilities of tech companies.
With encryption under fire, the implications stretch far beyond the UK, raising concerns about state surveillance, cybersecurity risks, and the future of digital privacy.
But what does this mean for you as an Apple user? And could this set a dangerous precedent for other tech companies like Google, WhatsApp, and Signal? Let’s break it all down.
What Is Apple’s Advanced Data Protection, and Why Does It Matter?
Apple’s Advanced Data Protection (ADP) is an end-to-end encryption feature that keeps iCloud backups completely private—even Apple itself can’t access them.
This applies to data like:
- iCloud device backups (iPhone, iPad, Mac)
- iMessage conversations stored in iCloud
- Photos, Notes, and Health data
- Safari bookmarks and reminders
With ADP enabled, only your devices hold the decryption keys, ensuring that no third party—including Apple, hackers, or governments—can read your data.
By forcing Apple to disable ADP for UK users, the government gains the ability to request access to your iCloud data under legal orders, something that wasn’t possible before.
This change fundamentally alters how secure your personal data is.
Previously, even if law enforcement had a warrant, Apple couldn’t access encrypted backups.
Now, UK users’ iCloud data is stored in a way that Apple can decrypt if required—just like regular cloud storage services.
How Does This Impact Security?
By removing ADP, the UK government is opening the door to several risks:
- ⚠️ Increased Hacking Risk – Without end-to-end encryption, your iCloud data is now more vulnerable to cybercriminals, state-sponsored hackers, and rogue insiders at Apple.
- ⚠️ Corporate Espionage – Businesses relying on iCloud face higher risks of data breaches, intellectual property theft, and targeted cyberattacks.
Why Is the UK Government Forcing Apple’s Hand?
The legal basis for this demand comes from the Investigatory Powers Act (IPA) 2016, also known as the Snooper’s Charter.
This law gives the UK Home Office sweeping surveillance powers, including the ability to:
- Force tech companies to remove encryption for law enforcement access.
- Demand access to private messages, phone records, and online activity.
- Require companies to keep their surveillance demands secret from users.
The Home Office argues that encryption protects criminals, making it harder for law enforcement to track down terrorists, child predators, and other serious offenders.
They claim that “lawful access” is necessary to maintain national security.
However, cybersecurity experts, privacy advocates, and even UK lawmakers are raising alarms about the consequences.
The Problem With “Lawful Access”
Creating a backdoor for law enforcement also creates a vulnerability that hackers and foreign governments can exploit.
🔻 In 2021, NSO Group’s Pegasus spyware exploited security flaws in Apple devices to hack journalists, activists, and politicians worldwide.
🔻 The 2023 LastPass breach exposed millions of encrypted password vaults when hackers targeted the company’s internal security systems.
🔻 In the US, the FBI’s push for encryption backdoors has repeatedly been rejected over fears of mass surveillance abuse.
By forcing Apple to weaken encryption, the UK is effectively making its citizens’ data more vulnerable to cyberattacks and espionage.
How Will This Affect Apple and Other Tech Companies?
Apple has long positioned itself as a privacy-first company, often taking a strong stance against government surveillance.
But with the UK threatening legal action, the company has little choice but to comply—or pull its services from the UK entirely.
Apple’s Global Privacy Reputation Is at Risk
By caving to UK demands, Apple risks losing credibility with users who trust its encryption promises. Will other governments now demand the same access?
Google, WhatsApp, and Signal Could Be Next
If the UK succeeds in pressuring Apple, other encrypted platforms—like WhatsApp, Signal, and Proton Mail—could be forced to remove encryption protections as well.
Tech Companies May Leave the UK
Companies like Proton Mail and Tutanota have already hinted they may exit the UK market rather than compromise their encryption standards. Could Apple follow?
Consumer Trust Is at Risk
A recent YouGov survey found that 68% of UK Apple users are considering switching to alternatives due to privacy concerns. If Apple loses trust, it could impact sales and adoption rates in the region.
What Can You Do to Protect Your Data?
Even though Apple has disabled ADP in the UK, you still have ways to secure your personal information.
🔒 Use Local Device Encryption – Store sensitive files on your iPhone or Mac with FileVault enabled, rather than relying on iCloud.
🔒 Encrypt Your iCloud Backups Before Uploading – Use tools like Cryptomator or VeraCrypt to encrypt data before backing it up to iCloud.
🔒 Use Alternative Cloud Services – Consider privacy-focused services like Proton Drive which offer end-to-end encryption.
🔒 Switch to a VPN and Encrypted Email – Services like Proton VPN and Proton Mail ensure your internet activity and emails remain private.
Final Thoughts: The Future of Encryption in the UK
This battle between Apple and the UK government is about more than just iCloud backups. It’s a defining moment for digital privacy that could set a precedent for tech companies worldwide.
If governments force companies to weaken encryption, it opens the door for mass surveillance, cyberattacks, and privacy violations.
Apple’s response—complying rather than pulling out of the UK—raises tough questions about the future of encrypted services. Will companies prioritize privacy, or will they cave to government demands?
For now, UK Apple users must assume their iCloud data is no longer private. The best course of action? Take control of your own encryption—because if governments get their way, you won’t have a choice in the future.





